‘Cryptojackers of the world, pack your bags and head to Japan!’
This seems to be the message a Japanese court delivered after a man who illegally operated cryptojacking software on his website was acquitted, Japanese publication The Mainichi.
According to the Yokohama District Court, handing punishment to the 31-year-old who works as a website designer is excessive. The man had been indicted for embedding the Coinhive cryptojacking software on his website without explicitly informing visitors that their computing resources would be used in mining cryptocurrency. Additionally, the court also ruled that Coinhive did not qualify as a computer virus.
In his ruling, Presiding Judge Toshihiro Homma argued that the man’s action of embedding Coinhive on his website between October and November in 2017 was not ‘socially intolerable’. However, the judge said the malware impacted users though to a minor degree. Prosecutors had sought a $900 fine.
Abuse of Service Leads to Coinhive Calling it a Day
Though the court ruled in his favor, the 31-year old can now no longer use Coinhive as it announced it was shutting down operations in late February. If the 31-year old managed to mine any Monero he will have to withdraw by April 30. The in-browser miner attributed its decision to constant abuse by malicious actors.
While Coinhive has become popular with cryptojackers, its initial mission was to serve as an alternative source of revenue to ads.
@coinhive_com #cryptojacking service to shut down in March 2019 after being abused by #malware gangs https://t.co/Q9xGx21uh3 #cryptomining #cybersecurity #blockchain
— Sentinel Protocol (@UPPSentinel) March 2, 2019
Despite the closure of Coinhive, which had more than 60 percent market share, cryptojacking is still expected to continue being a threat. This is because many other copycat cryptomining malware have sprung up over time.
Cryptojacking Threat is Growing
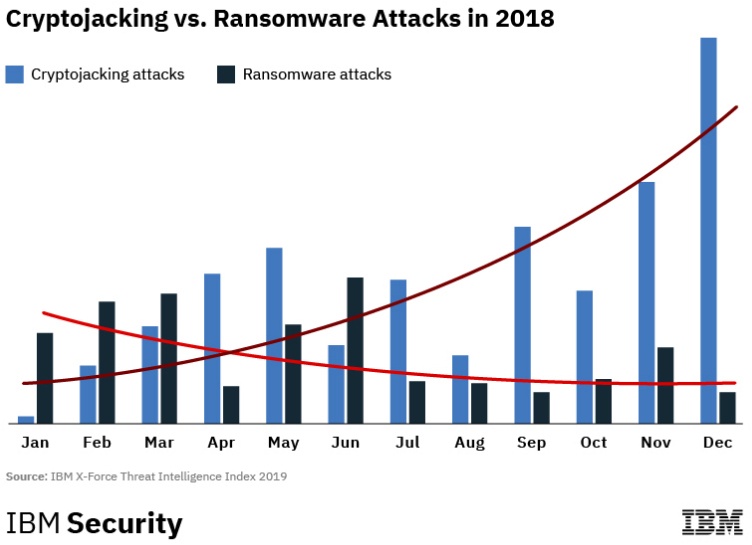
Research conducted by threat intelligence and research firm IBM X-Force indicated that cryptojacking incidences rose 450 percent in 2018. Per the IBM subsidiary, this coincided with ransomware attacks falling signaling that malicious actors were shifting tactics.
Other cybersecurity firms had even more alarming statistics. McAfee, for instance, estimated that cryptojacking malware had grown by 4,000 percent in 2018. The number of such malware rose from 500,000 in 2017’s fourth quarter to four million in 2018’s third quarter. These malware were not restricted to in-browser mining but were also installable on operating systems. Hardware such as routers, Internet of Things devices, IP Cameras and media players were other targets.
Tech Platforms Take the Fight to Cryptojackers
One of the most popular ways of distributing crypto mining malware has been through app stores. These malware disguise themselves as entertainment, educational or utility apps but they are in actual fact crypto miners. Most recently, Microsoft removed eight cryptojacking apps from its store after being notified by cybersecurity firm Symantec. On the surface, the apps were posing as mobile search engines, video downloaders and battery optimizers among others.
While tech platforms have made every effort to remove these malware from their platforms, some manage to escape detection because the cybercrime gangs are always changing tactics. Third-party solutions for these malware have included browser extensions which check for cryptojacking malware.